| Home | Sign up! | Projects | Seminars | Research Notes | Today's Lecture | About |
DB AdministratorEmail
ashay@dharwadker.org
| | Profile: My Students Database demonstrates the design and implementation of an online relational database management system (RDBMS) in Boyce-Codd normal form (BCNF). It provides a temporal data warehouse for storing information about my students' projects, seminars and research work. My Students Database also provides a search engine for performing elementary data mining tasks. Prof. Ashay Dharwadker's Courses (18): | Course | Semester | Grade | | | Algorithm Design - I | Fall 2000 | View | | | Algorithm Design - II | Spring 2001 | View | | | Data Structures | Summer 2001 | View | | | Probability & Statistics | Fall 2001 | View | | | Algorithm Design - I | Fall 2001 | View | | | Algorithm Design - II | Spring 2002 | View | | | Decision Analysis | Spring 2002 | View | | | Probability & Statistics | Summer 2002 | View | | | Algorithm Design - I | Fall 2002 | View | | | Probability & Statistics | Spring 2003 | View | | | Software Engineering | Spring 2003 | View | | | Information Systems | Fall 2003 | View | | | Database Systems | Fall 2003 | View | | | Algorithm Design - II | Spring 2004 | View | | | Computer Networks | Spring 2004 | View | | | Research | Summer 2005 | View | | | Research | Fall 2005 | View | | | Research | Spring 2006 | View | |
|
Project ID: 1
Course: Information Systems
Topic: Example - Web Browser
| Description: We designed a web browser using Visual C++ and MFC (Microsoft Foundation
Classes). The browser opens at the default home page http://www.google.com.
There is a text box into which the user can enter a new URL and a GO button
that takes the user there. There are BACK and FORWARD buttons that allow
the user to surf between previously visited sites. Here are the steps with
the initial MFC wizard:
-
Open Visual C++, File - New - Project Name: Browser
-
Single Document, Document/View Architecture Support
-
None
-
None, ActiveX Controls
-
Docking Toolbar, Initial Status Bar, Printing and Print Preview, Context
Sensitive Help, 3D Controls, Internet Explorer ReBars
-
MFC Standard
-
Base Class: CHtmlView, Finish
-
Build and Execute
Some further coding is required to make the buttons operational! The advantage
of making such a browser is that we can customize it suit our needs. For
example, I use my browser to connect to MySQL databases using ODBC! |
Project ID: 55
Course: Dynamical Systems
Topic: Julia Sets
| Description: Let X be a set together with a
function f
: X
→ X.
Given any x ∈
X, the iterates
f 1(x) = f (x)
f 2(x) = f ( f (x)
)
f 3(x) = f ( f
( f (x) ) )
.
.
.
are all well-defined elements of X. We define the orbit of
x ∈ X as the set { f
n(x)
| n = 1,2,3,... }. In this context (
X, f ) is called
a dynamical system. For example, the animation below shows the dynamical
system (C, z 2 ).
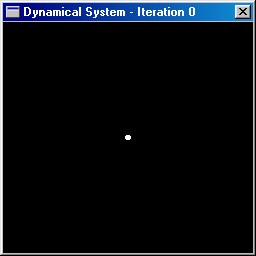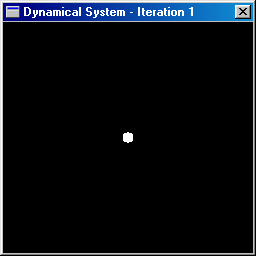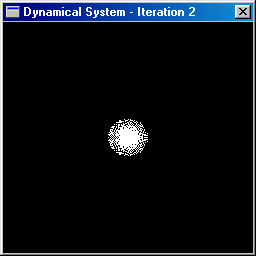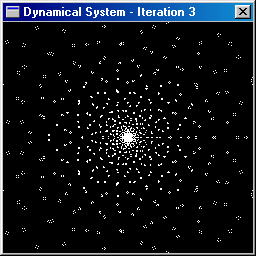
The white points are initially
inside a disc of radius 2 centered at the origin and 3 iterations are then
performed. Some of the orbits tend to remain bounded while others tend
to escape towards infinity.
Now let X= C ∪ {∞} be
the extended complex plane and consider rational functions f
(z)
= p(z) | q(z) where p,
q are
polynomials without any common factors. The filled Julia set of
the dynamical system ( C ∪ {∞},
p(z)
| q(z) ) consists of all points whose orbits are bounded
sets in the complex plane C. The
Julia set of the dynamical
system ( C ∪ {∞}, p(z)
| q(z) ) is the boundary of the filled Julia set. A filled
Julia set may be a connected set in the complex plane (aka Fatou region)
or a totally disconnected set in the complex plane (aka Cantor dust).
We first consider the case f (z) = z 2
+ c where c is a constant. It is a remarkable fact that the
corresponding filled Julia sets are connected (i.e. form Fatou regions)
if and only if c belongs to the Mandelbrot set. In fact, this can
be taken as a definition of the Mandelbrot set, shown below in Figure 1.

The Mandelbrot set (white)
shown on
[-1.5,0.5] × [-1,1] |
Seminar ID: 1
Course: Database Systems
Topic: Example - RSA Encryption
| Description: In reality, we would secretly select two very large primes P and
Q. For illustration, we
-
Select prime P=5
-
Select prime Q=7
-
Find E such that gcd(E,(P-1)*(Q-1))=1 and E%2!=0: Found E=5
-
Find D such that ((D*E)%((P-1)*(Q-1)))==1: Found D=5
The RSA Algorithm:
-
Encrypt(T)=pow(T,E)%(P*Q)
-
Decrypt(C)=pow(C,D)%(P*Q)
-
Your Public Key is (E,PQ). Tell Everybody Your Public Key!
-
Your Private Key is D. Keep Your Private Key Secret!
RSA Encryption:
Encrypt(1)=1 Decrypt(1)=1
Encrypt(2)=32 Decrypt(32)=2
Encrypt(3)=33 Decrypt(33)=3
Encrypt(4)=9 Decrypt(9)=4
Encrypt(5)=10 Decrypt(10)=5
etc.
For example, using the ASCII values of characters, the message THE_EAGLE_HAS_LANDED
can be encrypted using E and PQ to THJZJAGQJZHAXZQANIJI. This can be decrypted
back to the original message only by someone who knows D and PQ. To find
your private key D, a hacker needs to factor PQ into P and Q and there
are no known methods to do this in a realistic amount of time if PQ is
large!
-
Explain the above statement. Why does the hacker need to factorize PQ to
find your private key?
-
Find out how MySQL supports RSA Encryption. Look in the manual!
|
Research Note ID: 1
Course: Database Systems
Topic: Example - Relational Algebra
| Description: The design and implementation of My Students Database is based upon Codd's relational algebra. The eight operators for Codd’s relational algebra are:
1. Restriction: Returns a table containing all records from a specified table that satisfy a specific condition.
2. Projection: Returns a table containing all (sub) records that remain in a specified table after specified fields have been removed.
3. Product: Returns a table containing all possible records that are a combination of two records, one from each of two specified tables.
4. Union: Returns a table containing all records that appear in either or both of two specified tables.
5. Intersection: Returns a table containing all records that appear in both of two specified tables.
6. Difference: Returns a table containing all records that appear in the first but not the second of two specified tables.
7. Join: Returns a table containing all possible records that are a combination of two records one from each of two specified tables, such that the two records contributing to any given combination have a common value for the common fields of the two tables (and that common value appears just once, not twice in the resulting record).
8. Division: Takes two single-field tables and one double-field table and returns a table containing all records from one single-field table that appear in the double-field table matched with all records in the other single-field table.
|
|
Last updated on Wednesday, 26th March 2014, 04:23:01 PM.
Prof. Ashay Dharwadker
|
|

