| Home | Sign up! | Projects | Seminars | Research Notes | Today's Lecture | About |
Dev AgarwalEmail
dev_agarwal@rediffmail.com
| | Profile: I am currently pursuing a Bachelor’s degree in Computer Information Systems at Ansal Institute of Technology in affiliation with Tarleton State University (USA). I have acquired knowledge in C, C++, PHP, JAVA, HTML, MySQL and MFC applications. Besides academic activities, I am actively involved in Adventure sports and Mountaineering. Listening to Pink Floyd, Beatles and lounge music is also one of my favourite activities. I am proficient in Hindi and English. Prof. Ashay Dharwadker's Courses (2): | Course | Semester | Grade | | | Information Systems | Fall 2003 | View | | | Database Systems | Fall 2003 | View | |
|
Project ID: 27
Course: Database Systems
Topic: Music Database
| Description: The project on which I am currently working is a Music Database. At Present I am acquiring information regarding various Artists, their Albums, Date of Release, Song, Genre etc. I have also started building my Database.
FIELD TYPE COLLATION NULL KEY DEFAULT EXTRA
ARTIST
ano int(11) binary yes null
artist char(20) latin_swedish_ci yes null
COMPANY
FIELD TYPE COLLATION NULL KEY DEFAULT EXTRA
alno int(11) binary yes null
Album char(20) latin_swedish_ci yes null
company char(20) latin_swedish_ci yes null
genre char(20) latin_swedish_ci yes null
RELATION
(ano.alno) int(11) binary yes null
|
Seminar ID: 24
Course: Database Systems
Topic: SSL, FTP and Certificates
| Description: Jasdeep and I gave this Seminar on 6th November, 2003.
SSL stands for Secure Socket Layer Protocol. This was created by Netscape in order to secure all possible transactions between the servers and the Browsers
Certificate: A certificate, contains all the detailed information regarding the owner of the certificate such as his name, e-mail address, Certificate Usage, date of validity, Distinguished Name (DN) and the certificate ID of the person who certifies (signs) this information. It contains also the public key and finally a hash to ensure that the certificate has not been tampered with.
The following steps take place:
- First the web browser sends a public key along with a certificate.
- Then its checked whether the Certificate is genuine and is from a reliable source.
- After this the browser encrypts the random Symmetric encryption using the Keys along with the encrypted URL and the encrypted http Data.
- Now the server decrypts the Symmetric encryption using the private key and further uses it to decrypt the URL and http Data.
- Then the server sends the html document, http data encrypted along with symmetric keys.
- These Symmetric keys are used by the browser to decrypt the http data and html document thus displaying the required information.
 |
Seminar ID: 25
Course: Information Systems
Topic: Euler`s Formula
| Description: Jasdeep and I had given a seminar on Euler’s Formula and further on the basis of Euler`s Formula we had proved why there are exactly 5 Platonic solids.
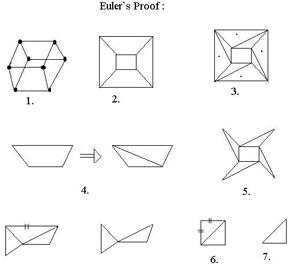
First We will prove Euler’s Formula which is
V + F - E = 2. (where E=Edges, V=Vertices and F = Faces).
- First take a cube (the proof for an arbitrary polyhedron is the same) and cut one face and spread it flat on a plane.
- Now we have same number of V,E and one Face is reduced.
i.e. If we can prove V-E+F=1 then it is also true for V-E+F=2.
- First "Triangulate" to a Simplicial Complex (as shown in fig-3).
- So now E = E + 1 , F = F + 1 and V = V.
- Now remove the edges of the boundary triangles that do not belong to the inside triangle.(as shown in fig-5)
- E becomes E -1 ,F becomes F-1 and V remains same.
- Further eliminate the edges of the boundary triangle that do not belong to the inside triangle (as shown in fig-6).
- Now count the number of Edges ,Vertices and Faces and Place it in the Equation.
You will get V- E+F=3-3+1=1 Hence Proved.
|
Seminar ID: 41
Course: Database Systems
Topic: Why Are There Exactly 5 Platonic Solids?
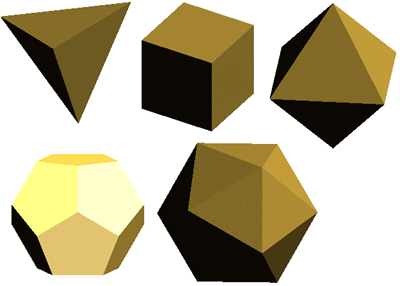
| Description: Proof: Take any Platonic Solid.
- Face is some regular polygon or n-gon with r edges meeting at each vertex.
So n>=3 and r>=3.
- Count the Edges:
N*F=2E( Because each edges makes 2 faces so each edge is counted twice in n*F).
- Lets take an example of a Cube.
N*F=2E
4*6=2*12 (Proved)
r*V=2E
- By Euler’s Formula
V- E + f=2
(2 E / r) – E + (2 E/n ) =2
(n*F = 2E => F =2E/n)
(r*V =2E => V =2E/r)
- Placing the values of F and V)in equation .
After Simplifying we get ((1 / r) +(1/n) =(1/2)+(1/E)).
Now n>=3 and r>=3 but both n and r cannot be >3.(this you can find out by placing the values of n and r greater than 3 in the equation).
- Case 1:
N=3 => (1 / r ) = ( 1/6) + (1/E)
when r =3 E=6 its tetrahedron , r=4 E =12 its octahedron and when r = 5,E=30 its icosahedron.
- Case 2:
R=3 =>(1/n) = (1/6) + ( 1 / E).
When n=3,E=6 its tetrahedron=4, E=12 its cube and When n =5 ,E=30 its dodecahedron).
There cannot be any other possible values thus it is proved that there are exactly 5 platonic solids.
|
Research Note ID: 43
Course: Database Systems
Topic: Encryption in SQL
| Description: The ENCRYPT function returns a value that is the result of encrypting data-string-expression. Generally the password used for encryption is either the password-string-expression value or the encryption password value.
- Data-String-Expression
An expression that returns a CHAR or VARCHAR value to be encrypted. The length attribute for the data type of data-string-expression |is limited to 32663
- Password-String-Expression
An expression that returns a CHAR or VARCHAR value with at least 6 bytes and no more than 127 bytes (SQLSTATE 428FC). The value represents the password used to encrypt the data-string-expression.
- Hint-String-Expression
An expression that returns a CHAR or VARCHAR value up to 32 bytes that will help data owners remember passwords (for example, 'Student' as a hint to remember 'Dev'). If a hint value is given, the hint is embedded into the result and can be retrieved using the GETHINT function
- This example uses the encryption password value to hold the encryption password.
SET ENCRYPTION PASSWORD = 'Dev54321';
INSERT INTO student(SSN) VALUES ENCRYPT('21');
-
This example explicitly passes the encryption password.
INSERT INTO student(SSN) VALUES ENCRYPT('21,'Dev54321','');
-
The hint 'Student' is stored to help the user remember the encryption password of 'Dev').
- INSERT INTO student(SSN) VALUES ENCRYPT('21','Student','Dev');
|
|
Last updated on Wednesday, 26th November 2003, 05:03:45 PM.
Prof. Ashay Dharwadker
|
|

